
Navigate New York DFS Section 500 with Confidence
Section 500 compliance isn't just about having policies on paper—it's about building operational cybersecurity programs that work in practice. Many organizations struggle to bridge the gap between regulatory language and real-world implementation.
Understanding NYDFS Section 500
The New York Department of Financial Services Cybersecurity Requirements (23 NYCRR 500) establish minimum standards for protecting consumer data and ensuring the safety of New York's financial services industry. If you're licensed or regulated by NYDFS, compliance is mandatory.
Complex Requirements: Translating regulatory language into practical controls is challenging
Documentation Gaps: Many firms have policies but lack operational evidence of compliance
Resource Constraints: Small firms need efficient compliance without enterprise-level budgets
Your Practical Compliance Partner
We don't just advise—we help you build, document, and maintain cybersecurity programs that meet Section 500 requirements while fitting your operational reality.
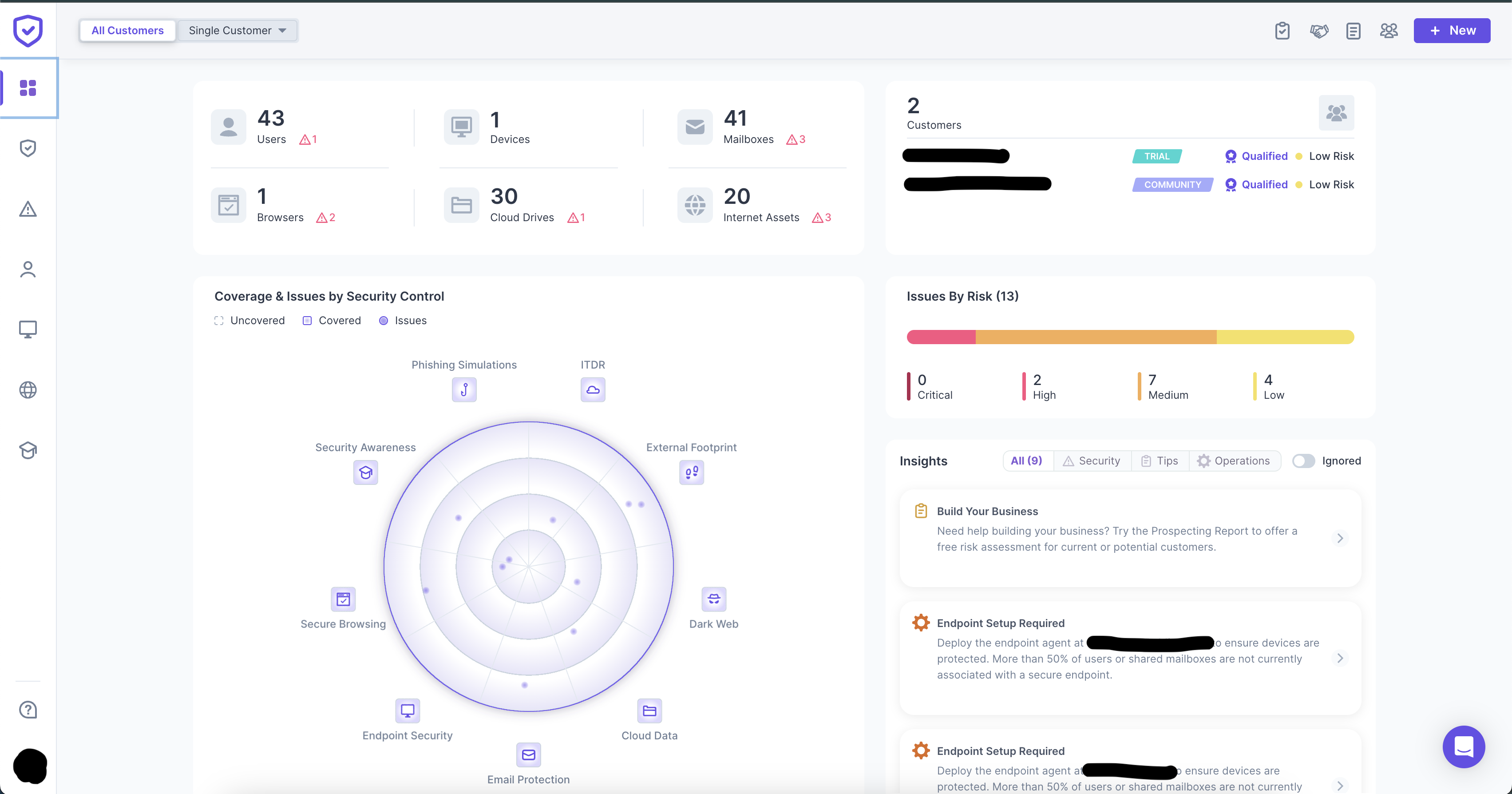
How We Support Your Compliance
Actionable Control Translation
We translate Section 500 requirements into clear, implementable controls your team can execute
Program Development & Documentation
Build comprehensive cybersecurity programs with documentation that meets NYDFS expectations
Risk Assessments
Conduct thorough risk assessments aligned with regulatory standards and your business reality
Ongoing Compliance Support
Maintain readiness with continuous guidance, updates, and operational compliance support
Specialized Expertise
We focus exclusively on cybersecurity compliance for financial services, with deep expertise in NYDFS Section 500 and related state regulations.
We Understand Your Challenges
Real problems. Proven solutions. Immediate results.
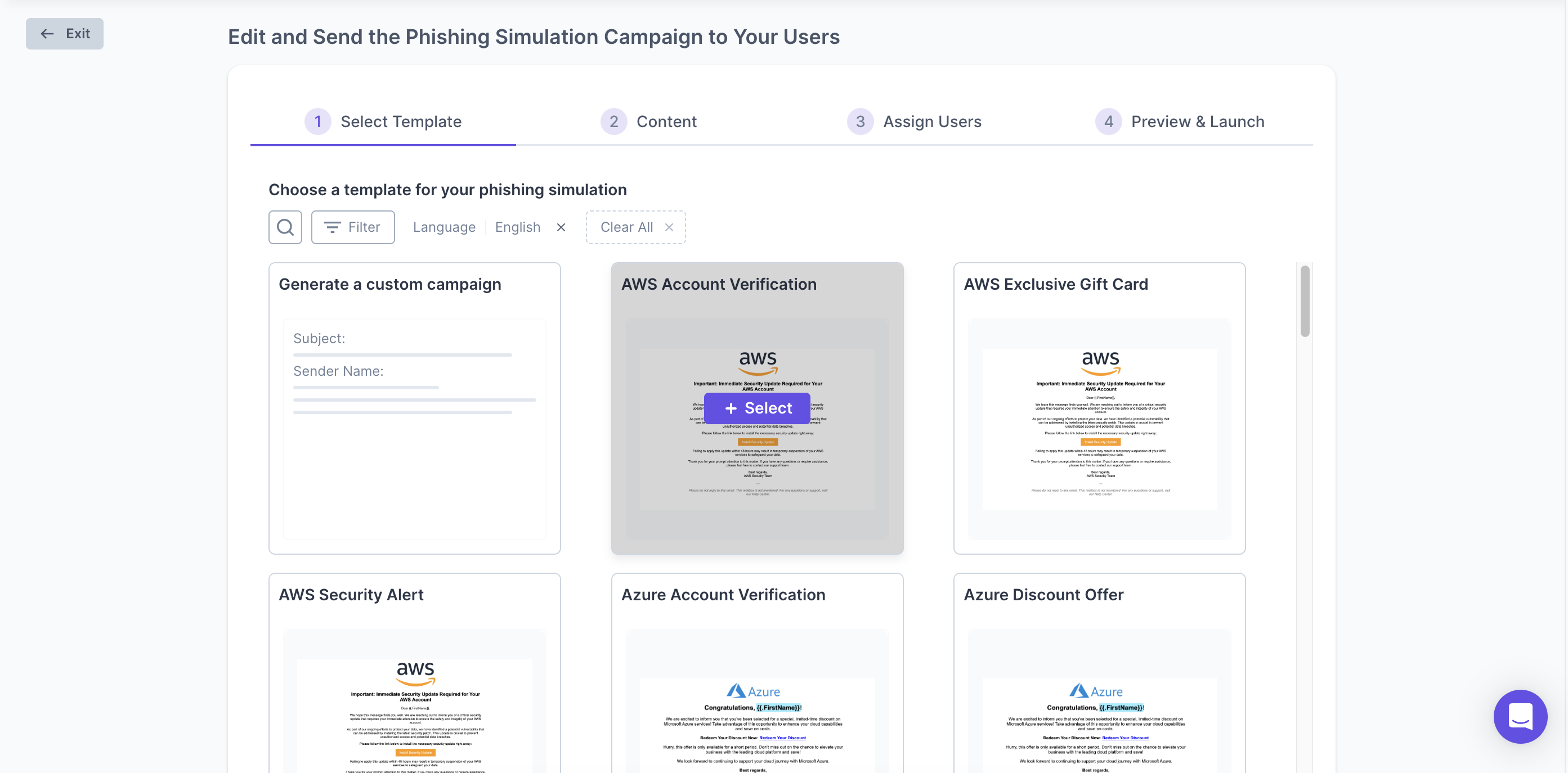
Phishing Protection
The Problem
65% of cyber attacks start with phishing
Our Solution
Test your team before hackers do
- Company-wide phishing test
- 2-week protection trial
- Vulnerability report
24/7 Protection
The Problem
Threats don't sleep - neither should your security
Our Solution
Round-the-clock monitoring & instant response
- 24/7 monitoring
- Instant response
- Monthly reports
Volume discounts available for 20+ users
Get Protected
Risk Assessment
The Problem
State examiners require recent security reports
Our Solution
Get examination-ready in 48 hours
- Full audit
- Action plan
- Compliance check

Policies & Procedures
The Problem
Missing policies = compliance failures
Our Solution
36+ ready-to-use security policies
- 36+ policies included
- Fully customizable
- GLBA compliant
Have a Unique Challenge?
Let's discuss your specific security needs - we'll create a custom solution
Schedule CallWhat Our Clients Say
"Saved us from a $500K ransomware attack. Best investment we ever made."
"Setup took 2 hours. Haven't worried about cyber threats since."
"Passed our regulatory exam with flying colors thanks to their compliance tools."
Trusted & Certified
Don't Wait for an Attack
Financial firms are attacked every 39 seconds. Get protected before you become the next target.
Live Threat Feed
Ransomware Attack
CRITICALCredit Union in Texas
2 min ago
Phishing Email
HIGHInvestment Firm in NY
5 min ago
Data Breach Attempt
CRITICALMortgage Company in CA
8 min ago
Malware Detection
MEDIUMFinancial Advisor in FL
12 min ago
847 attacks blocked today
