
Compliance Starts With aRisk Assessment
Before you can fix your security gaps, you need to find them. Our cybersecurity risk assessment is the critical first step to protecting your firm and passing your next state examination.
Get a comprehensive vulnerability scan, compliance gap analysis, and a prioritized action plan — delivered in 7 days or less.
Security Risk Assessment
What you'll receive
Navigate New York DFS Section 500 with Confidence
Mandatory for all NYDFS-regulated firms — we help you move from paper policies to operational compliance.
Common Challenges
- Complex regulatory language that's hard to operationalize
- Documentation gaps between policy and practice
- Limited resources to meet enterprise-level requirements
How We Help
- Translate complex 23 NYCRR 500 requirements into clear, actionable controls
- Build & document cybersecurity programs that satisfy examiners
- Conduct risk assessments aligned with NYDFS standards
- Ongoing compliance monitoring & support to maintain readiness
- Tailored for small to mid-sized financial services firms
Want the full breakdown?
Explore every Section 500 requirement and how we address it.
We Understand Your Challenges
Real problems. Proven solutions. Immediate results.
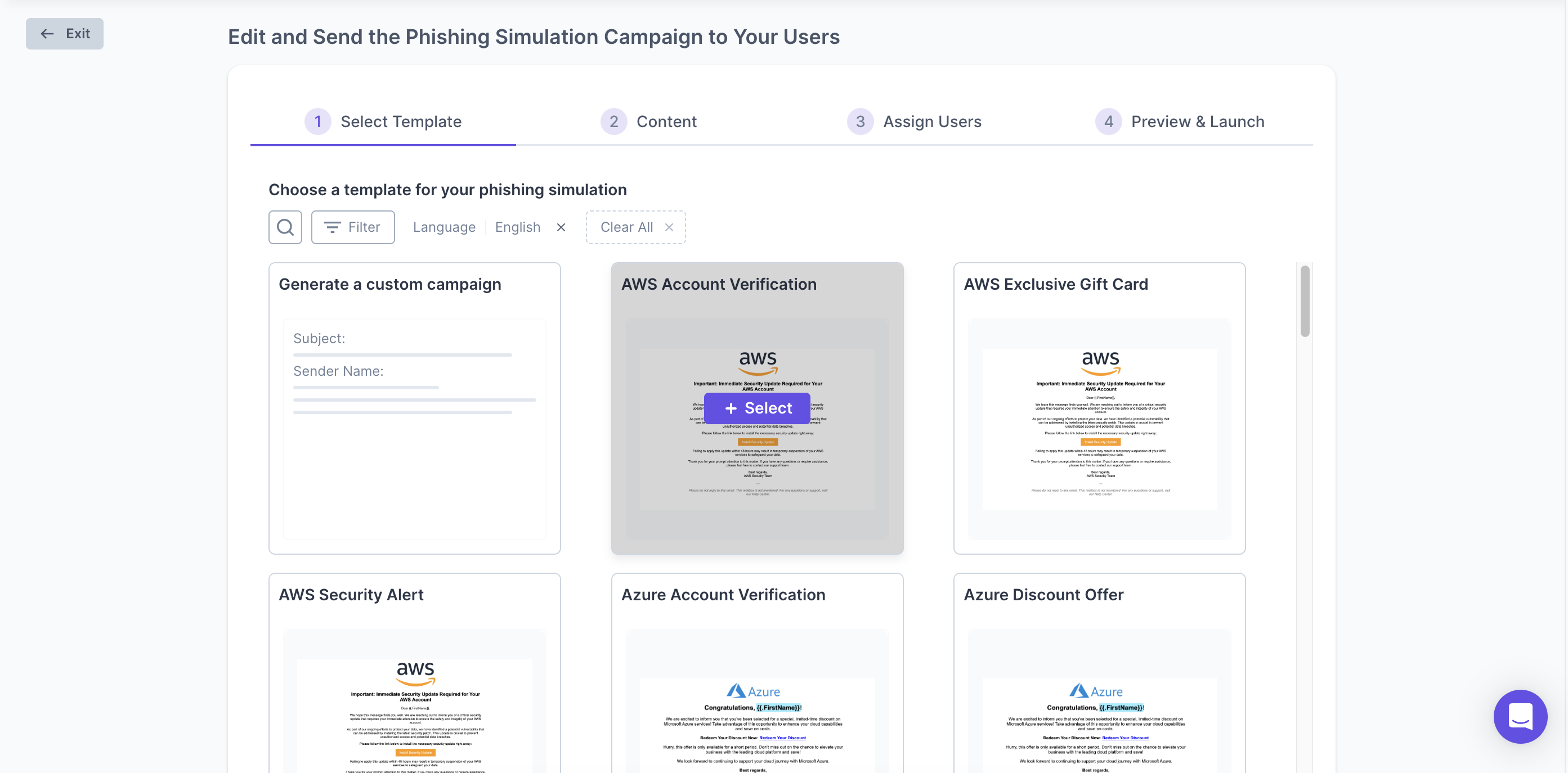
Phishing Protection
The Problem
65% of cyber attacks start with phishing
Our Solution
Test your team before hackers do
- Company-wide phishing test
- 2-week protection trial
- Vulnerability report
24/7 Protection
The Problem
Threats don't sleep - neither should your security
Our Solution
Round-the-clock monitoring & instant response
- 24/7 monitoring
- Instant response
- Monthly reports
Volume discounts available for 20+ users
Get Protected
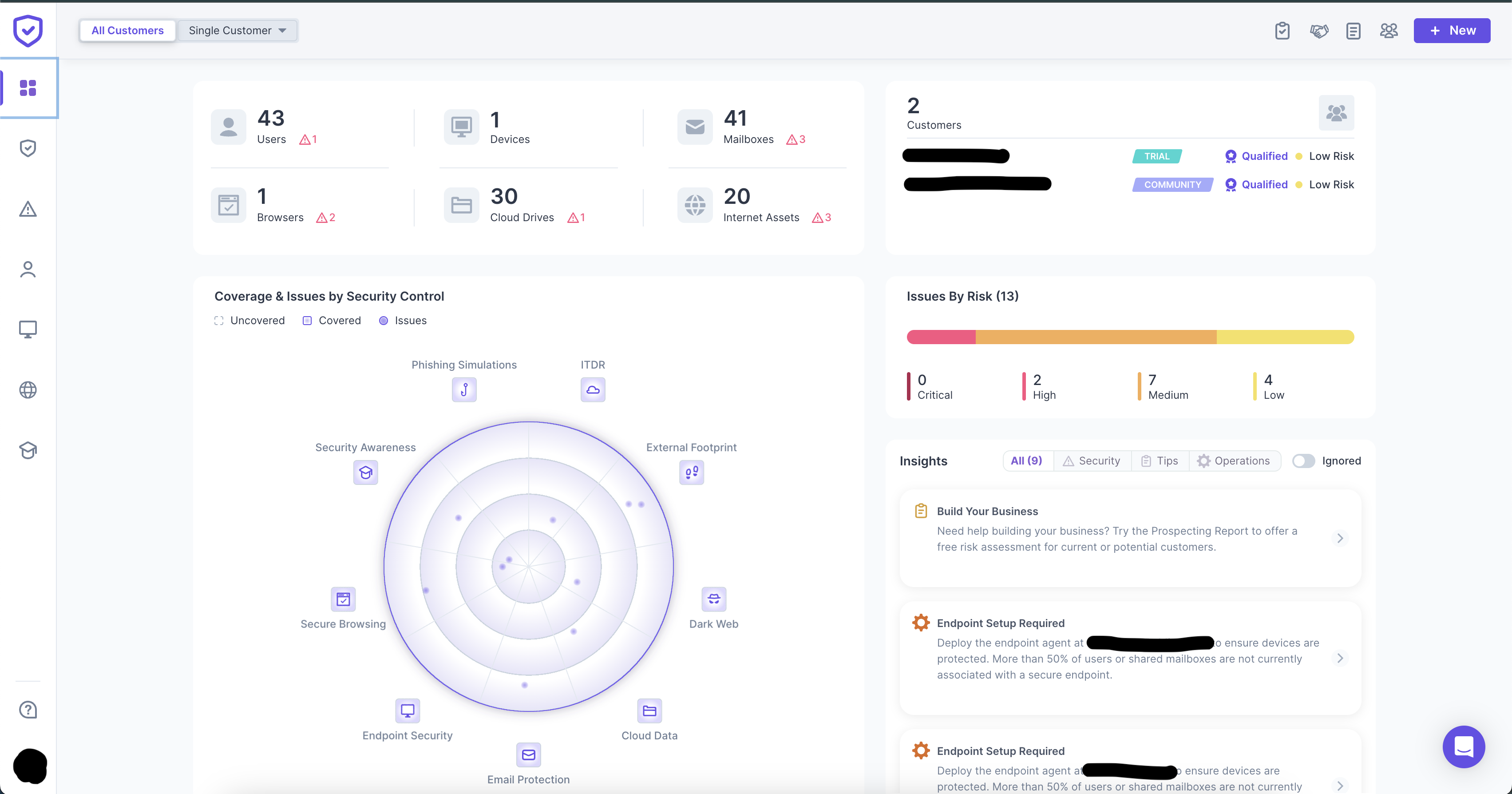
Risk Assessment
The Problem
State examiners require recent security reports
Our Solution
Get examination-ready in 48 hours
- Full audit
- Action plan
- Compliance check

Policies & Procedures
The Problem
Missing policies = compliance failures
Our Solution
36+ ready-to-use security policies
- 36+ policies included
- Fully customizable
- GLBA compliant
Have a Unique Challenge?
Let's discuss your specific security needs - we'll create a custom solution
Schedule CallWhat Our Clients Say
Trusted & Certified
Don't Wait for a Breach to Take Action
The average cost of a data breach in 2024 is $4.88 million. Every day without proper cybersecurity controls increases your risk exposure and potential regulatory penalties.
of small businesses close within 6 months of a cyber attack
Average regulatory fine for non-compliance with DFS Section 500
Required notification timeframe for cybersecurity events under DFS rules
We use cookies & tracking technologies
We use cookies and similar technologies (including Google Analytics and Contentsquare) to understand how visitors use our site, improve your experience, and for analytics purposes. By clicking "Accept All", you consent to our use of these technologies. You may decline non-essential tracking at any time.
