Your cart is currently empty!
Prevent data breaches, leakage, and loss with encryption, secure networks, and continuous IT system monitoring for financial compliance.
Data Loss & Leakage
Overview:
Data loss or leakage occurs when sensitive information is accidentally deleted, lost, or disclosed to unauthorized parties. This can happen through user error, insecure file transfers, inadequate backups, or a security breach.
Why Small Financial Firms Are Vulnerable:
Financial data is one of the most valuable types of information for cybercriminals, and even unintentional exposure can lead to severe regulatory and reputational consequences. Smaller firms may lack robust data classification and protection policies, increasing the likelihood of accidental mishandling.
How MortgageMoat.com Helps:
We implement strong data protection measures, including encryption, secure file-sharing solutions, and clear data handling policies. We also help you establish procedures for secure disposal of sensitive information and maintain compliance with applicable data protection regulations.

with Upgrades Available for More Complete Protection. Screenshot Taken by Ethan Houley.
Unmonitored Systems & Shadow IT
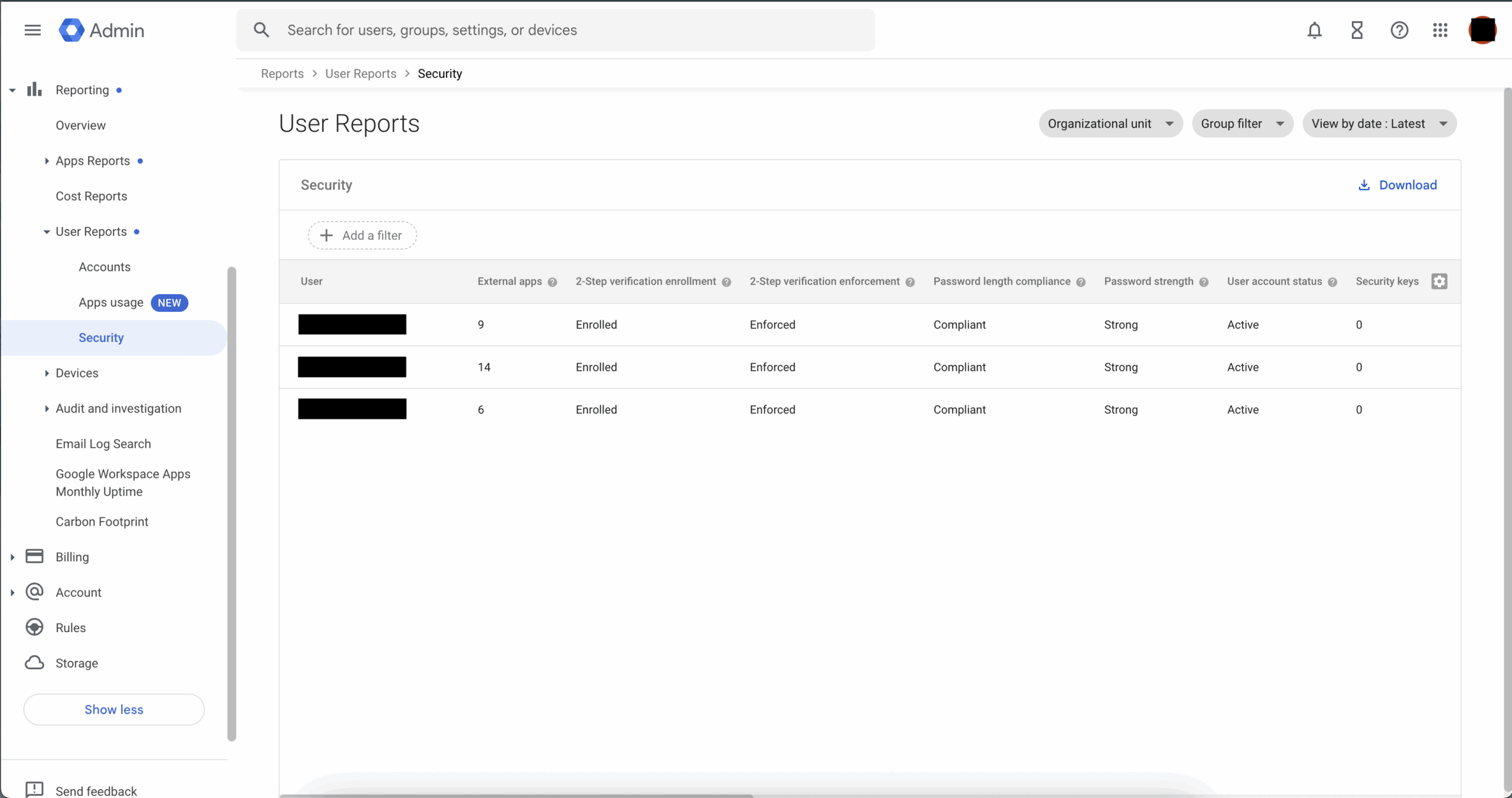
Indicating Which Users Are Verified, Compliant, and from within Your Organization. Screenshot
Taken by Ethan Houley.
Overview:
Shadow IT refers to software, devices, or services used by employees without official approval. These tools often bypass the organization’s security measures and may store sensitive data in unsecured locations. Unmonitored systems are company-approved assets that lack active oversight, making them potential blind spots for attackers.
Why Small Financial Firms Are Vulnerable:
Without centralized oversight, unauthorized tools can proliferate quickly, creating gaps in your security coverage. Unmonitored systems can allow malware or intrusions to persist undetected for months, especially if logging and alerting are not in place.
How MortgageMoat.com Helps:
We identify and eliminate unauthorized tools, consolidate approved technology, and implement monitoring systems that track suspicious activity across your network. This provides continuous visibility and helps you maintain compliance.
Unsecured Networks & Remote Access
Overview:
Remote work relies heavily on internet connections and remote access tools, such as VPNs and remote desktop software. If these are misconfigured or unsecured, they can be exploited to gain unauthorized access to internal systems.
Why Small Financial Firms Are Vulnerable:
Employees working from home or traveling may connect over unsecured Wi-Fi networks, making them susceptible to interception. Remote access tools configured without strong authentication and encryption can give attackers a direct route into your systems.
How MortgageMoat.com Helps:
We secure all remote connections with strong encryption, multi-factor authentication, and properly configured VPNs. Our remote access policies ensure that only authorized users and devices can connect, and that logging of all sessions occurs for compliance purposes.
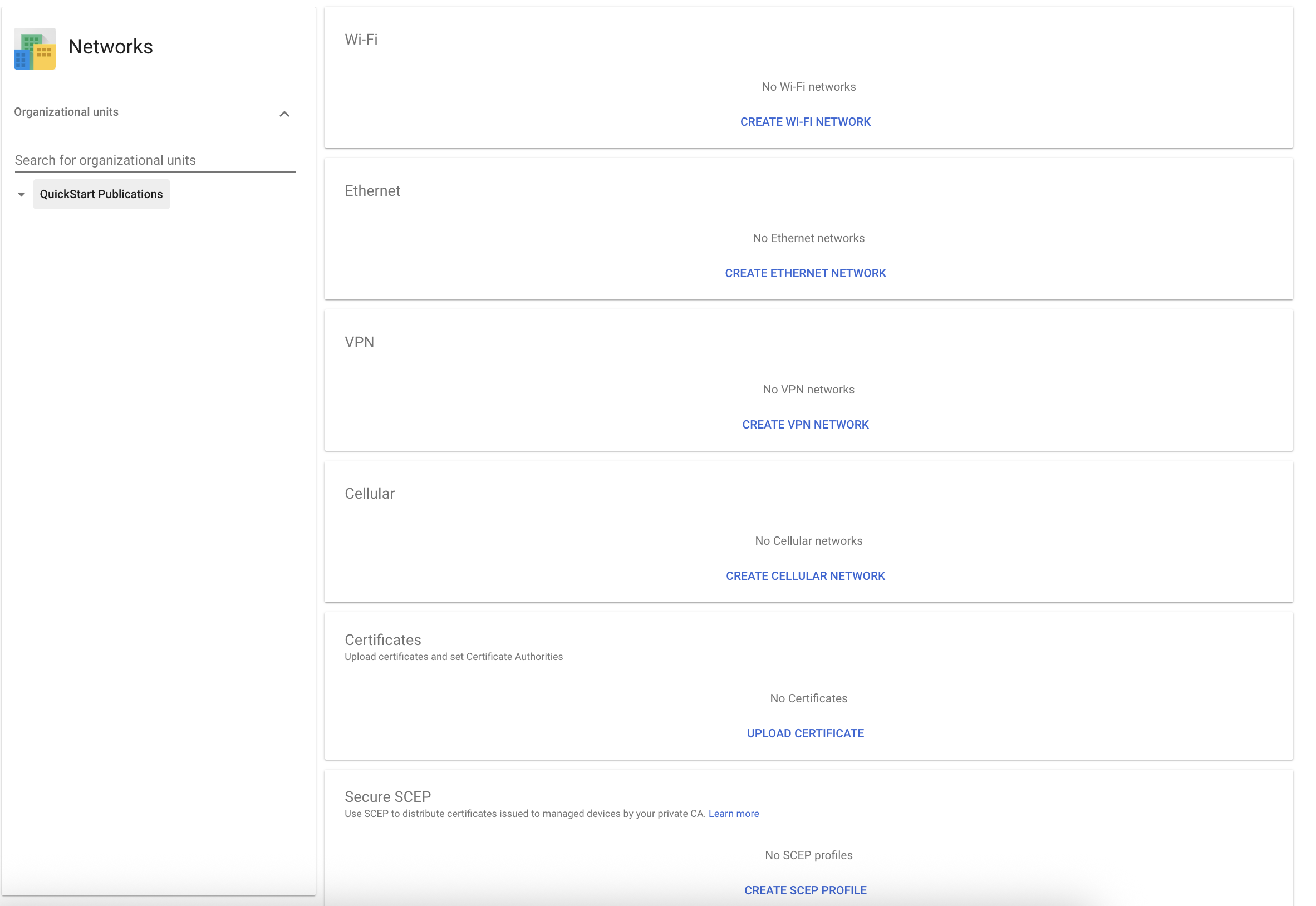
this Panel, from Wireless to Ethernet to Cellular. Control Network Security Certificates and VPN
Settings. Screenshot Taken by Ethan Houley.
