Your cart is currently empty!
Protect your financial firm from phishing, social engineering, and insider threats with targeted cybersecurity training and compliance procedures.
Phishing & Social Engineering
Overview:
Phishing and social engineering are attacks that target people, not technology. Criminals send emails, text messages, or make phone calls that appear to come from trusted sources, manipulating recipients into clicking malicious links, opening infected attachments, or sharing confidential information. Social engineering tactics often involve urgency, authority, or familiarity to lower defenses and bypass skepticism.
Why Small Financial Firms Are Vulnerable:
In smaller organizations, employees often handle multiple responsibilities and may be pressed for time, making them more susceptible to well-crafted phishing attempts. The financial industry is a prime target because attackers can directly monetize stolen credentials or sensitive data. A single successful phishing attack can compromise email accounts, client records, or financial systems.
How MortgageMoat.com Helps:
We deliver specialized training for employees and managers that uses real-world examples to teach recognition of phishing and social engineering tactics. Our policies include clear verification procedures for handling sensitive requests, and we provide simulated phishing exercises to keep staff prepared year-round.
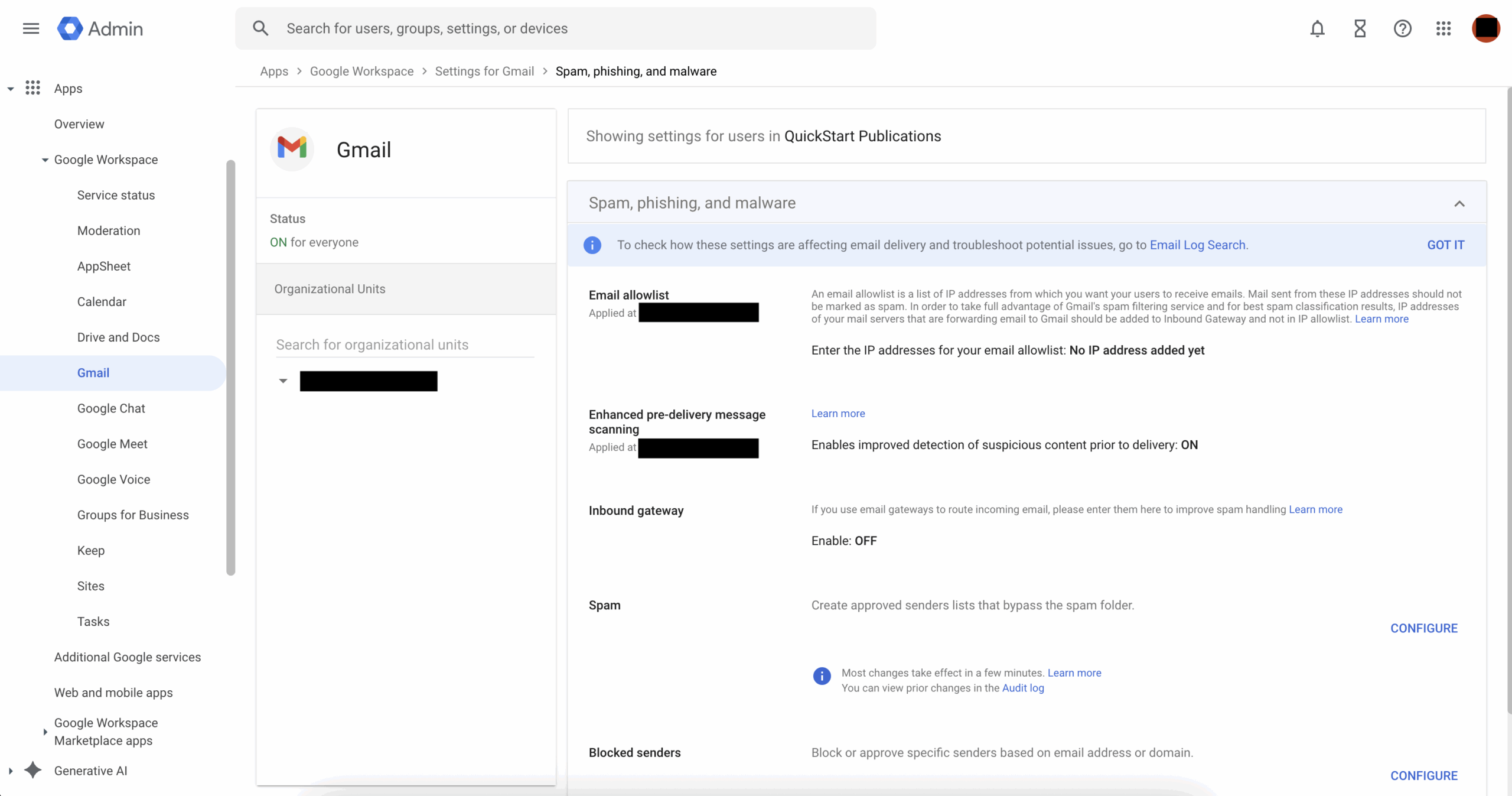
These Settings Are Advanced Options in the Settings for Gmail, Which Are Controlled from the
Same Section of the Admin Console. Screenshot Taken by Ethan Houley.
Business Email Compromise
Business Email. Screenshot Taken by Ethan Houley.
Overview:
BEC attacks involve criminals impersonating executives, partners, or vendors to trick employees into transferring funds or sending sensitive information. These emails often look authentic and may come from compromised accounts, making them extremely difficult to detect. Unlike phishing, BEC typically doesn’t use malicious links or attachments—relying instead on trust and authority to manipulate victims.
Why Small Financial Firms Are Vulnerable:
Smaller firms often rely heavily on email for client and vendor communication, and may not have layered authentication measures in place. Without email authentication protocols like DMARC, SPF, and DKIM, it’s easier for attackers to spoof legitimate senders. Financial transactions processed by small firms can be significant enough to be attractive targets but may not trigger large-institution fraud detection systems.
How MortgageMoat.com Helps:
We implement email authentication protocols to make spoofing more difficult and set up secure workflows for approving financial transactions. Our training programs teach staff how to recognize suspicious requests and confirm legitimacy before sending money or sensitive data. We also perform regular email security assessments to ensure systems stay protected.
Insider Threats
Overview:
Insider threats occur when employees, contractors, or vendors misuse their legitimate access to systems and data. This misuse can be intentional—such as stealing client data for personal gain—or accidental, like sending confidential information to the wrong recipient. Because insiders already have authorized access, their actions often bypass traditional security defenses.
Why Small Financial Firms Are Vulnerable:
In smaller firms, employees often have broader access rights due to resource limitations. Offboarding processes may be less formal, leaving accounts active longer than necessary. Without regular monitoring, unauthorized activity can go unnoticed, leading to data breaches, compliance violations, and reputational harm.
How MortgageMoat.com Helps:
We design access control policies that limit privileges to the minimum necessary for each role and conduct regular reviews to identify outdated accounts or unnecessary permissions. Our monitoring solutions detect unusual activity, enabling quick intervention before damage is done. We also provide training on secure data handling to reduce accidental insider incidents.
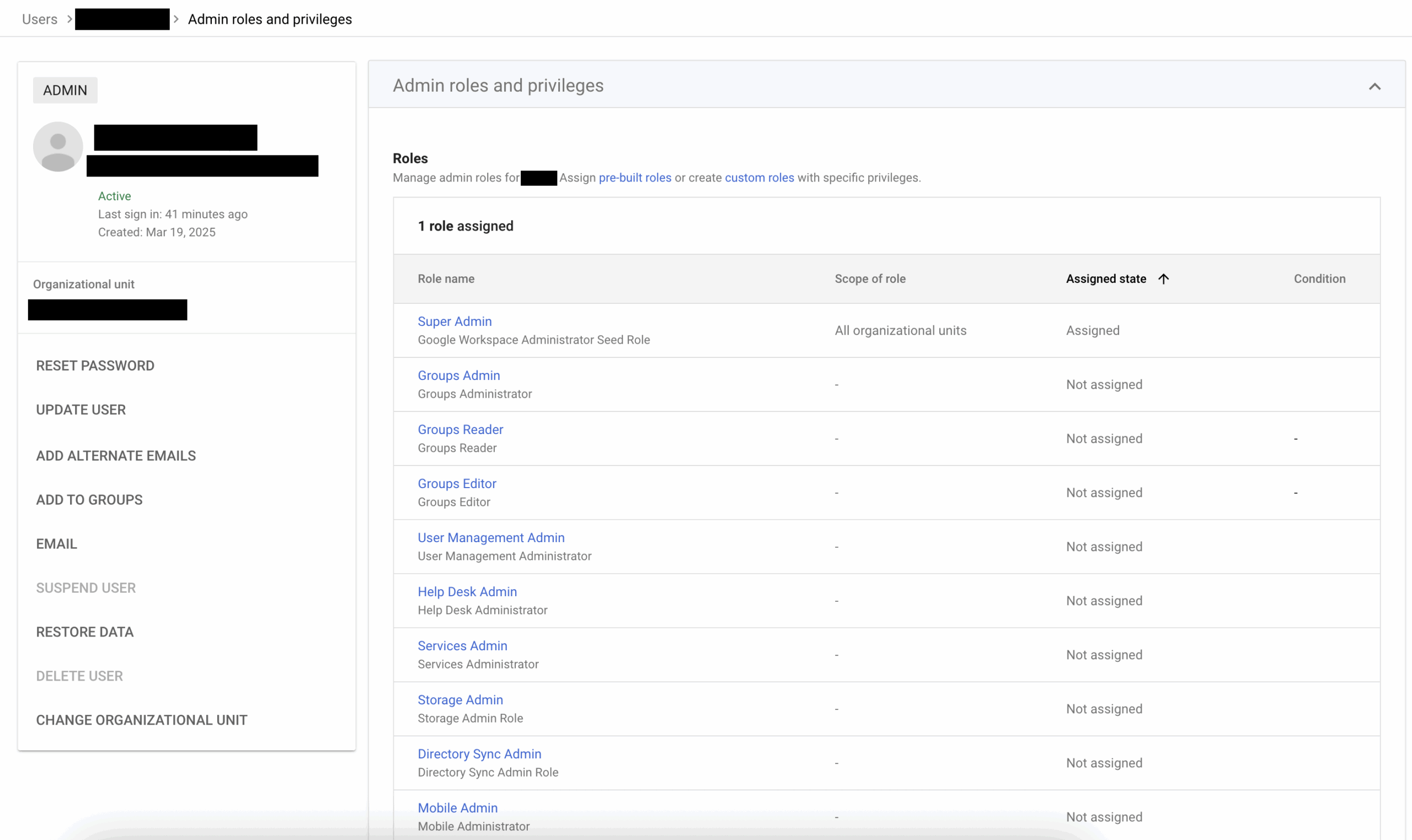
You Have Full Control Over Each User’s Roles and Permissions. Screenshot Taken by
Ethan Houley.
